Understanding API and its authentication methods

By now, you could have realised that every automation is all about moving and transforming data between different platforms.
For example, if you remember the Instagram Follower Count Tracker automation:
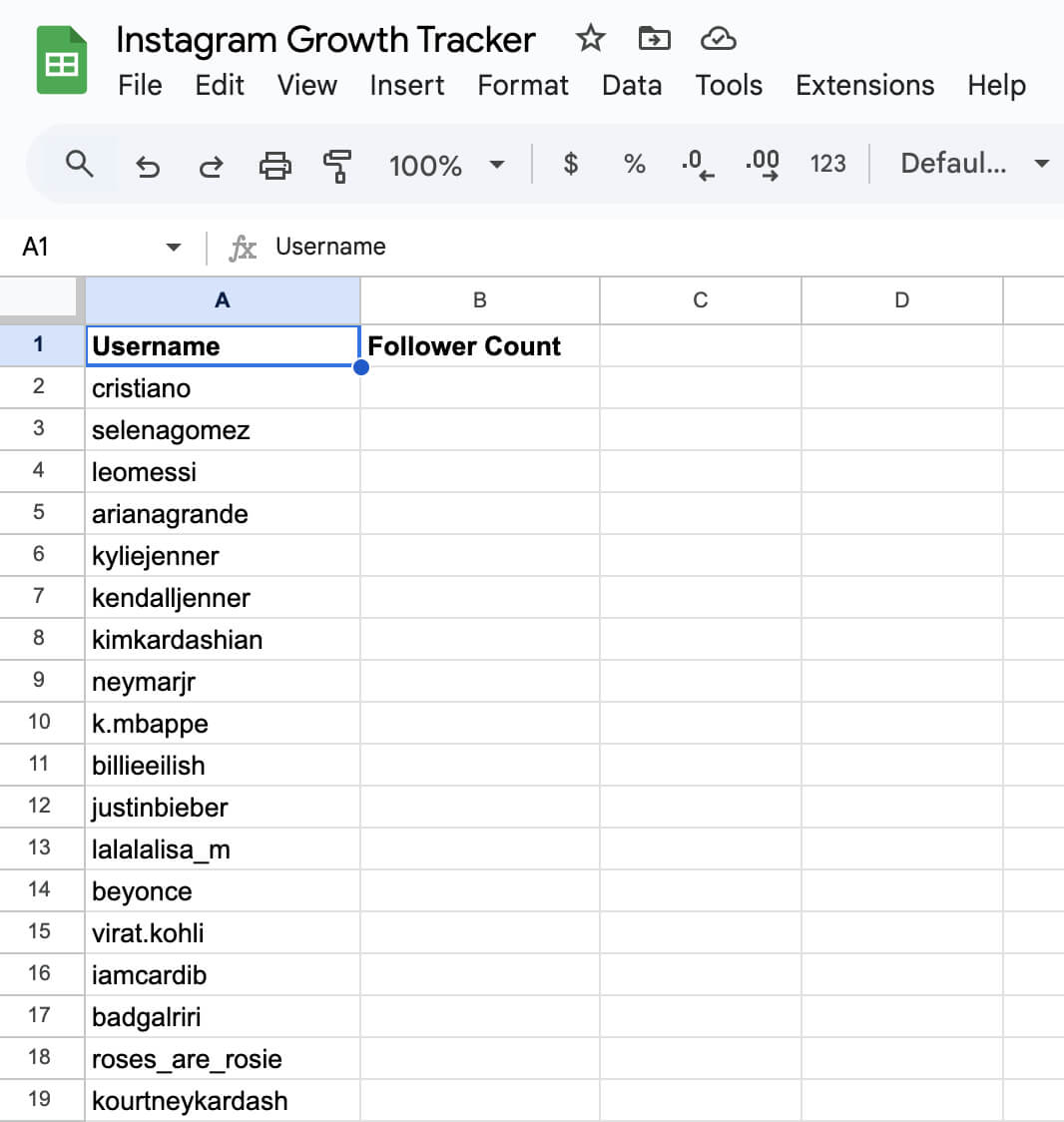
1) We are getting a list of Instagram usernames from a Google Sheet
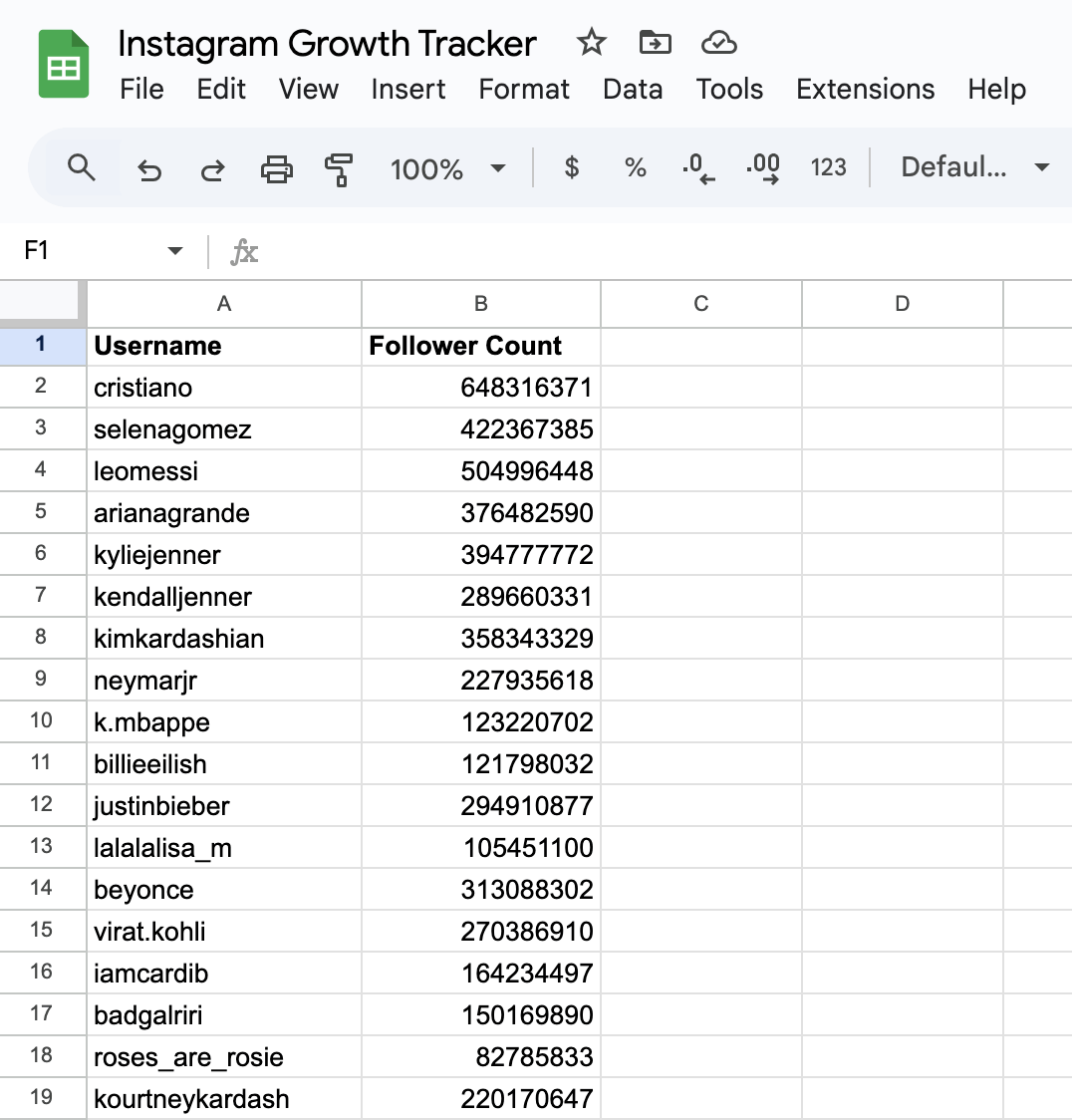
2) Next, we are fetching follower counts for these usernames from Instagram automatically
3) Finally, we are updating the Google Sheet with the follower count for each username automatically
If you observe, the automation depends on connecting with two different platforms and sharing data between them:
- Google Sheets
To be more precise:
- We must connect to Google Sheets platform, select the tracking spreadsheet with the list of usernames and fetch those usernames
- Next, we need to connect to Instagram for retrieving the follower count of respective usernames and save the follower count data somewhere
- Finally, we must connect back to Google Sheets platform for updating the Google Sheet with the follower count for each username
But now comes a couple of important questions:
- How do we connect with third-party platforms like Google Sheets to get or update their data?
- How do we share the data we fetch from one platform with another platform?
The answer to the first question is something called an API.
The answer to the second question is using an automation tool like make.com.
Understanding API
A platform creates an API to let us use its features and data, even when not using the platform's own app or website.
In other words, the API of a specific platform will help us connect with the platform to:
- Fetch their data with some restrictions
- Update their data with some restrictions
- Delete their data with some restrictions
- The list goes on and on…
For example:
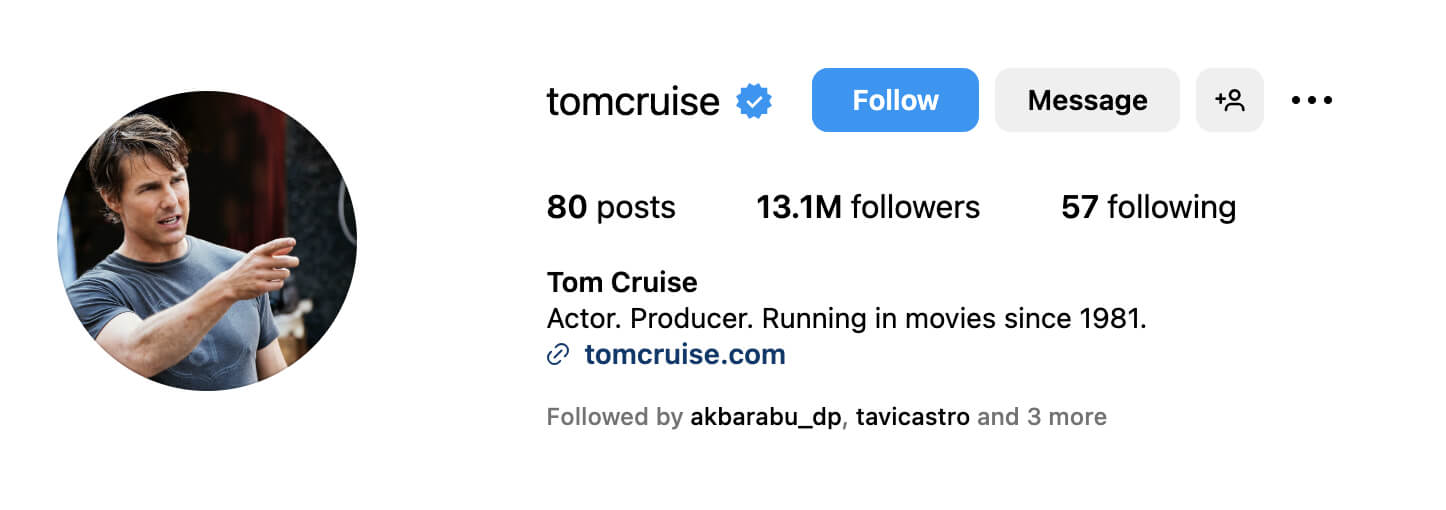
1) To get the follower count and other details of a profile, we need to use the Instagram API to connect to the Instagram platform and provide the username of a profile:
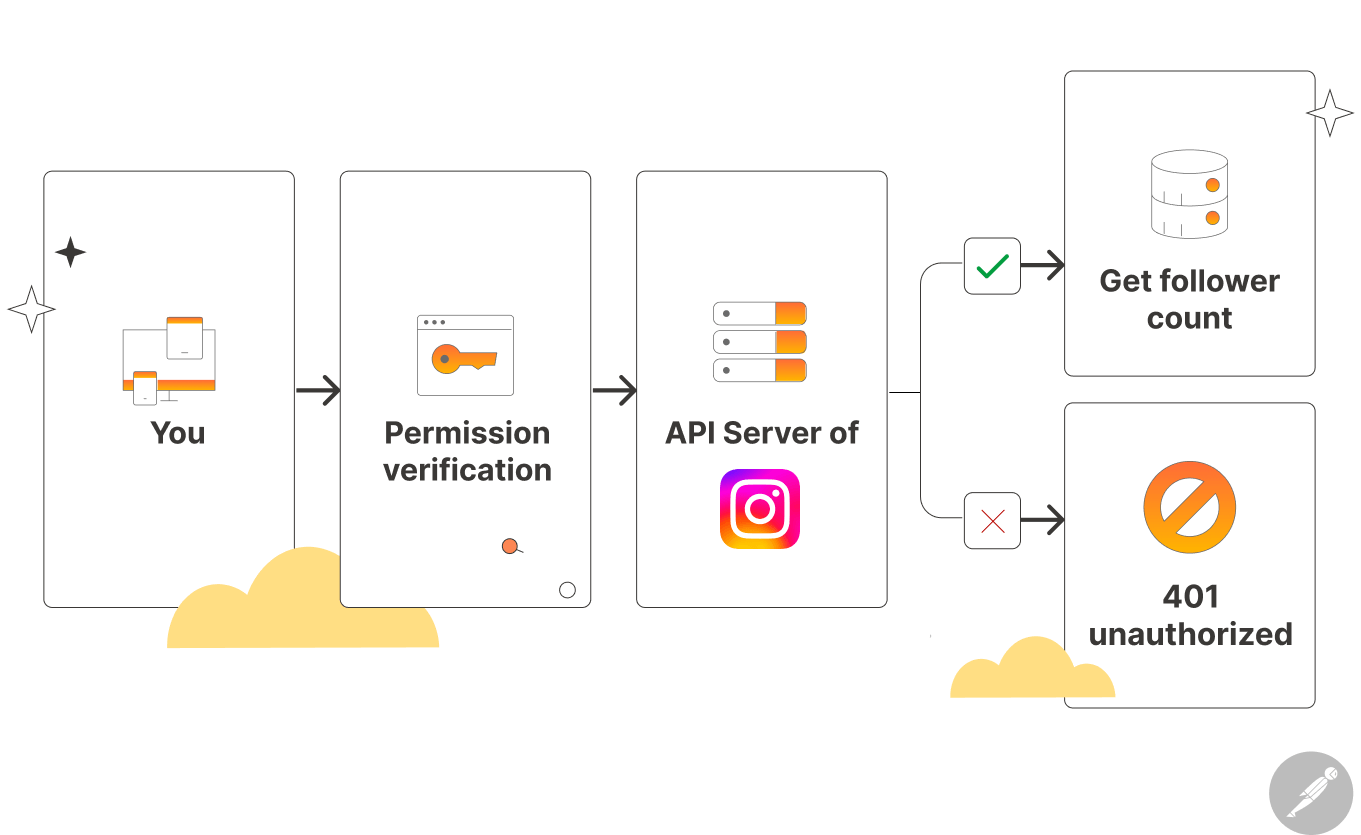
You can also perform other activities such as replying to comments, uploading reels, etc.
Similarly, we need to use the Google Sheets API to connect to a spreadsheet and performs actions on such as:
- Adding a row
- Updating a row
- Deleting a row
You get the idea, right?
Long theory short: When a platform exposes its API, they're technically saying to us that:
“Hey, if needed, use our API to safely access our features and data. Also, you don't have to log into our app or website. You can use your own app. Of course, you should follow our rules and requirements for using our API. If you don't, we can't let you use our API.“
But now comes another important question.
Do we let a stranger use our house and bathroom?
“Nope! I can't allow that.”
Yep, even I can't do that.
Similarly, we are a stranger to platforms like Google Sheets, Instagram, etc.
We don't own or build these platforms.
So, how does a platform allow us to use its API to get access to its features and data?
The answer is, the platforms don't let us their API just like that.
We need to get permission from the platform to use their API.
APIs have restrictions too.
Let me elaborate…
Authentication: Getting Permission to use an API
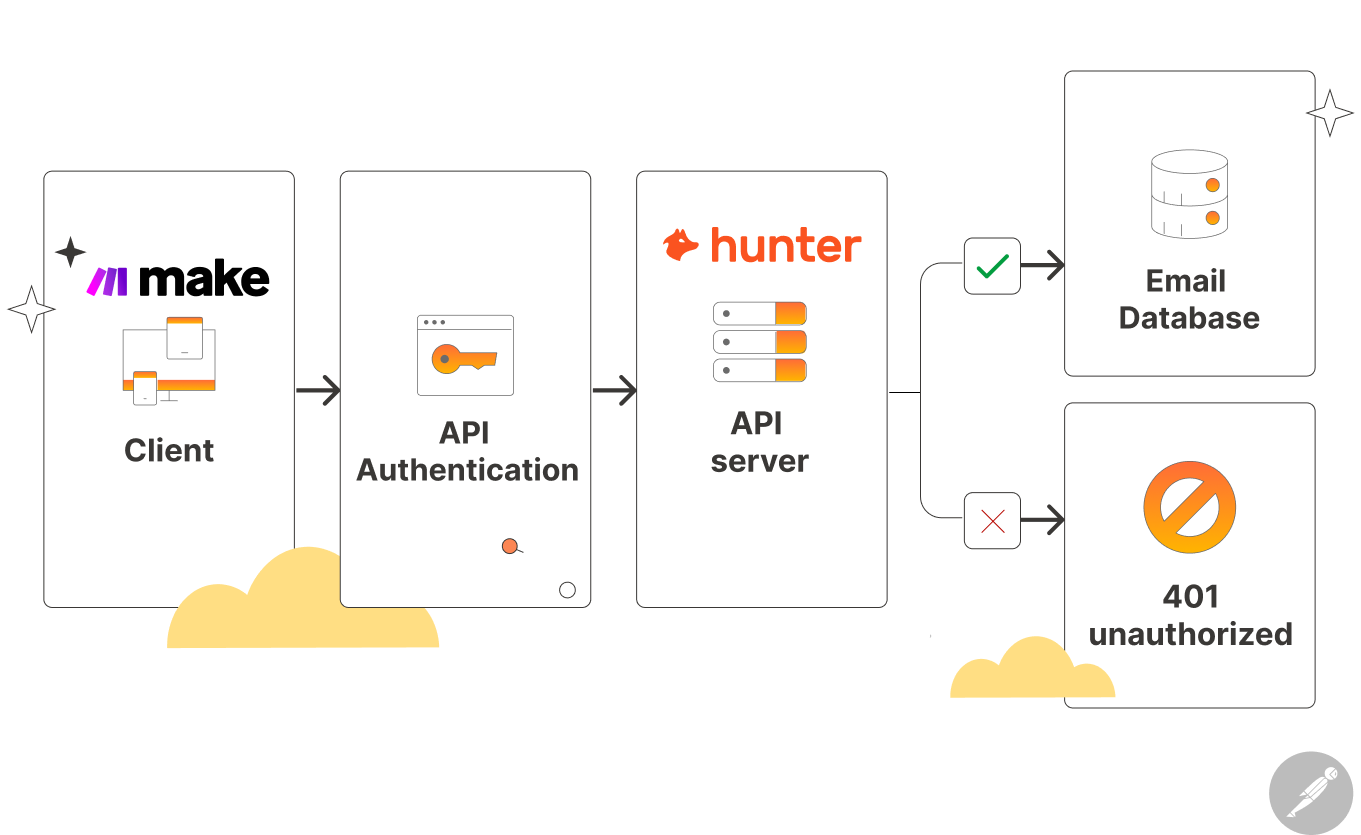
Platforms exposing their API is not a normal thing.
It is powerful because the API is exposing the platform's features and data.
And you can use it in any way.
For example, Hunter.io provide emails of business owners for your outreach campaign.
And they expose their API so that you can get access their functionality like email finder without logging into Hunter.io:
So, let me ask you something.
What's actually stopping us from creating a competitor service to Hunter and start charging people for valid emails?
Technically, nothing.
Honestly, you can build a successful business around it and some people are doing it already.
But, is it fair for Hunter to allow people to use its API without any security and make people like us their competitor?
No, right?
This is why platforms that expose their API put restrictions on how we can use their API so that:
- We don't become their competitors by using their data
- We don't abuse their servers and data centres
And they put these restrictions with the help of:
- API Authentication — Permission to use their API
- Rate limits — For example, we are allowed to use their API only a certain number of times every hour. This will keep their servers up and running for other users.
- Finally, billing you for using their API
For example, Convertio is a service that helps you convert your Word document into a PDF and other different formats.
They expose their API for free to help you automatic this document format conversion process.
But they put a limit that you can use their API only for 25 minutes in a day.
If you want to use their API for a longer period that 25 minutes, you can buy one of their paid packages. This will make sure you don't become their competitor.
Also, they require you to log in to get permission to use their API.
This is to keep us from abusing their functionality and crashing their servers.
If you observe, API Authentication is just like entering an invite-only exclusive restaurant.
If you're trying to enter an invite-only restaurant, you would need an invitation card, right?
Without the invitation card, the bouncer will stop you from entering:

Similarly, you can't start using an API directly.
We need to authenticate with a platform to start using its API services.
This is all good, but how do we perform this authentication?
There are many ways, but here are two popular methods of authentication:
- API Key authentication
- OAuth authentication
API Key authentication
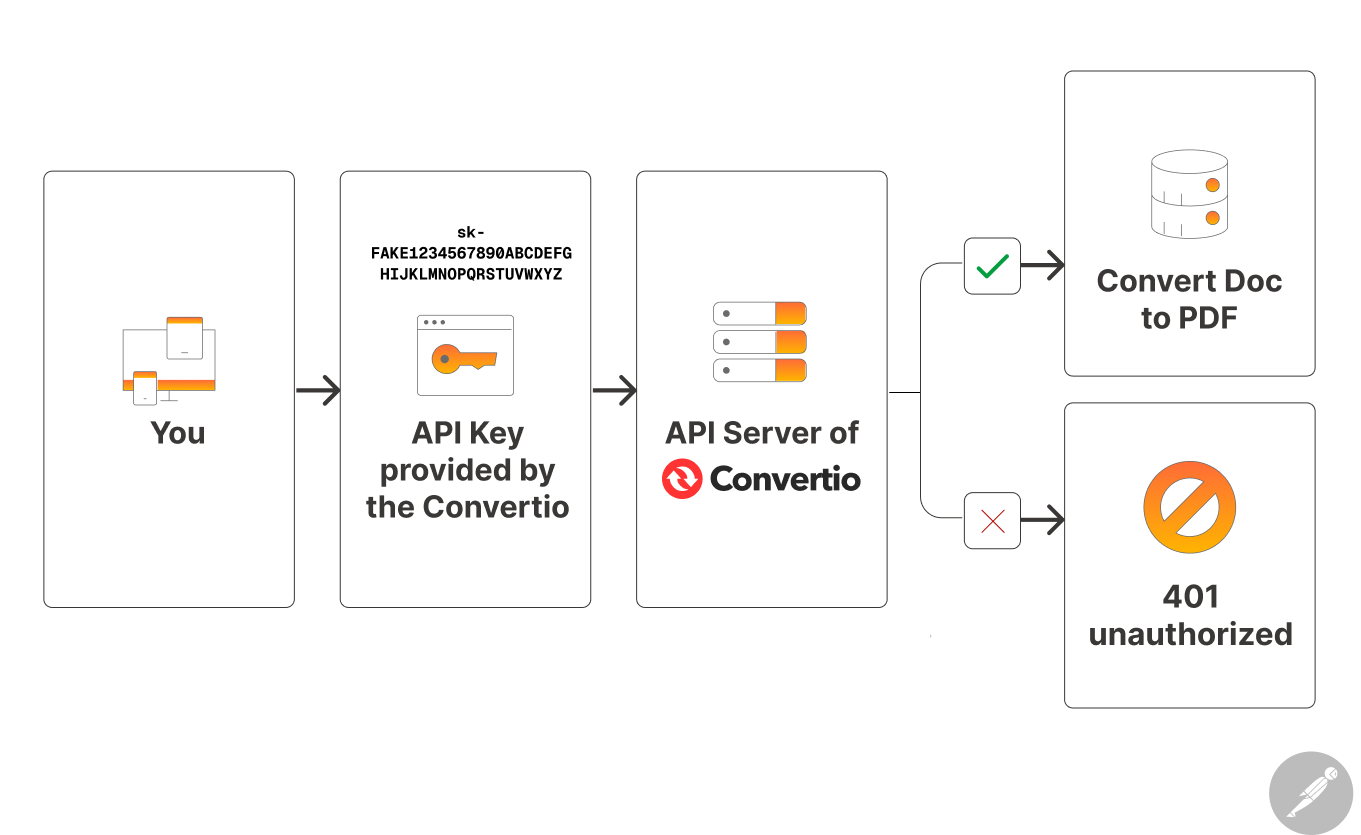
This is the easiest way to authenticate yourself with the platform.
An API key is nothing but a string that is made up of characters and numbers.
For example:
sk-FAKE1234567890ABCDEFGHIJKLMNOPQRSTUVWXYZMany platforms create an API key for you as soon as you create an account with them.
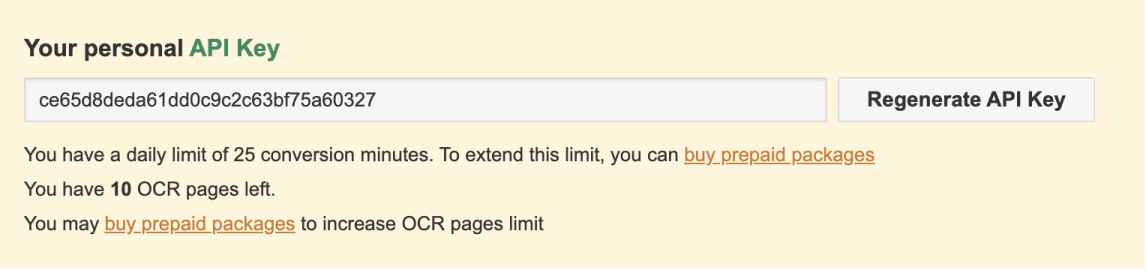
For example, Convertio provides your personal API key when you create an account with them:
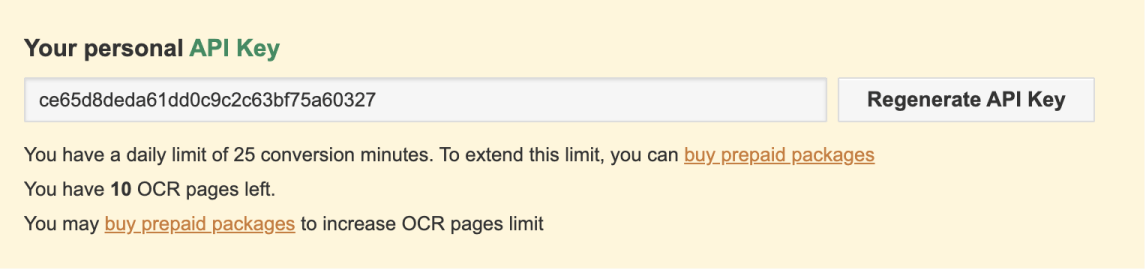
Anyway, once you have API key of a platform, you have to use it when requesting to access the platform's features and data.
If the API key is valid, the platform will allow you to use its features and data.
That's how easy it is to authenticate using the API key method.
Having said that…
Security Alert! 🚨
If you're not careful, it is easy to expose your API keys to hackers or freeloaders.
An API key is just a piece of text, after all.
You can think of API keys like your credit card numbers.
Do you ever share your credit card number publicly?
No, right?
Similarly, while using APIs of different platforms, you should:
- Never share them publicly
- Never save them in plain text files
- Never push them to public code repositories
- Never post them in screenshots
“But bro, you have shared your Convertio API key in the screenshot above.”
Nice, catch :P
I did it for demonstration purpose and deleted that key before posting the screenshot here.
I am smart you know :D
“Hmmmm.”
Anyway, security concerns are the primary reason why some platforms prefer you to use OAuth authentication for using their features and data.
OAuth authentication
OAuth is a token-based authentication system that allows users to grant third-party applications access to their accounts without exposing their login credentials.
Instead of sharing usernames and passwords, OAuth issues access tokens that allow apps to perform authorized actions on a user's behalf.
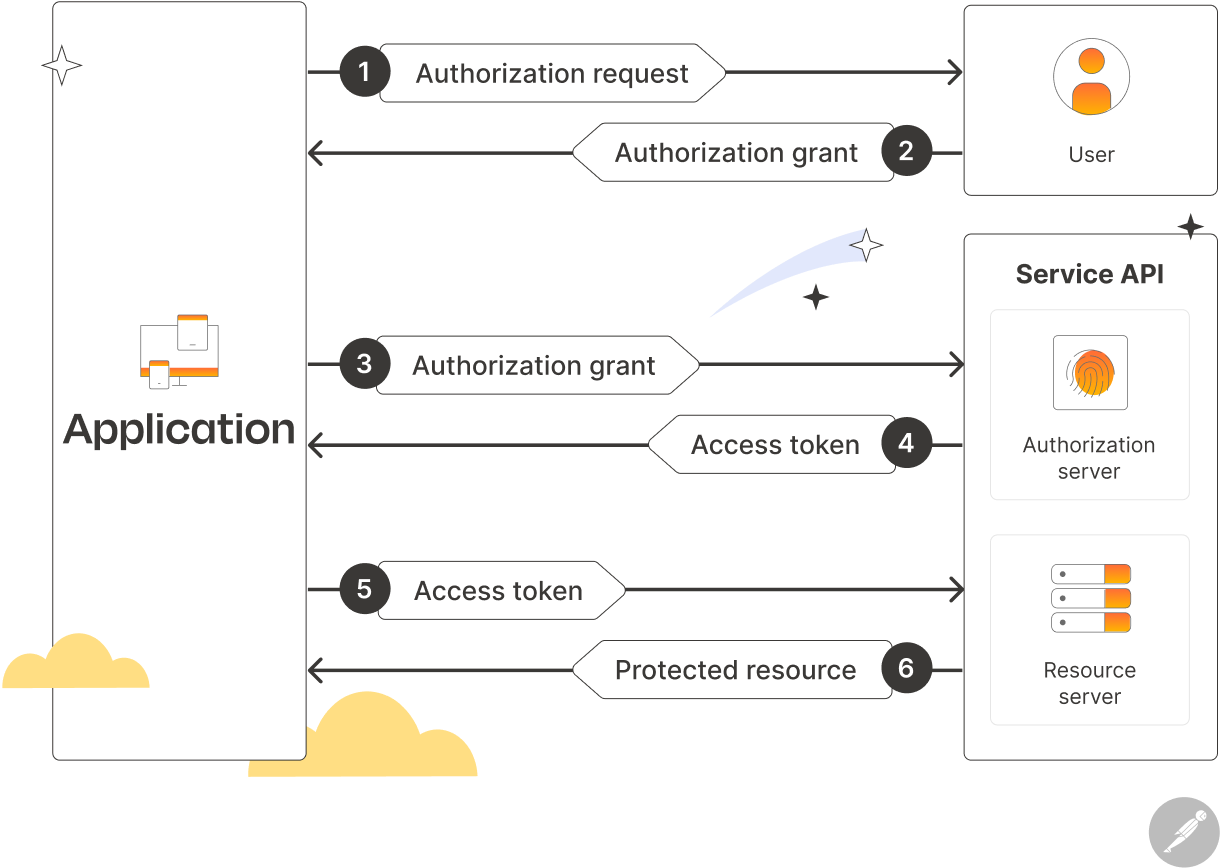
How OAuth Works
- Token Expiry & Refresh – Access tokens typically expire after a set duration, requiring refresh tokens for extended access.
- User Authorization – The user initiates login through a third-party provider (e.g., Google, Facebook, or GitHub).
- Token Exchange – Instead of sharing login credentials, the provider issues an access token to the requesting application.
- Restricted Access – The application can only perform actions permitted by the token's scope (e.g., reading user profile data but not modifying account settings).
Real-world examples
Make.com enables users to sign up using their Google account to simplify the login process and eliminate the need to create a separate password.
This approach enhances security by reducing password reuse and minimizing the risk of credentials being leaked or stolen.
Automation example: Imagine you want to automatically post content on Facebook and want to use Make.com as the automation platform.
To achieve this:
1) You log into Facebook through Make.com automation interface
2) Facebook then asks you, “Is it okay if Make.com uses your Facebook account to post content?”
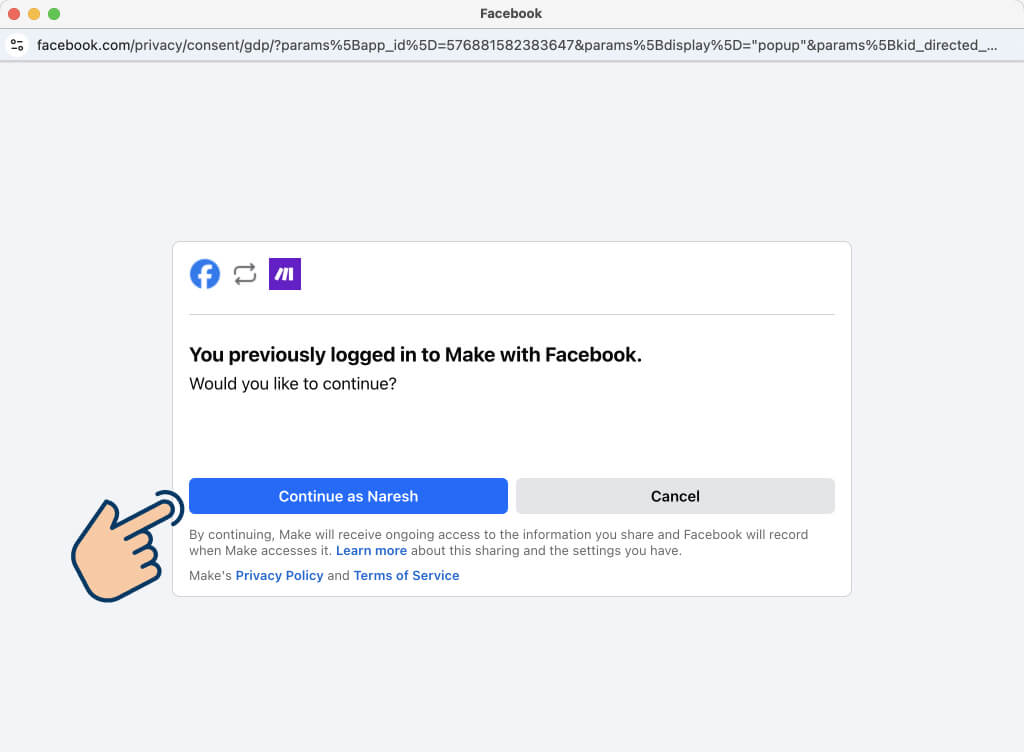
3) When you say continue, Make.com can now use Facebook API temporarily and post content automatically for you without using Facebook's own app or website.
This is safer compared to API key authentication because you don't need to share any secret codes (API keys) or login credentials of the platform with Make.com.
You are providing permission yourself by clicking buttons you see on the screen.
Anyway, we will see both the API keys authentication and OAuth authentication in action once we start building real-world automations throughout this course.
Choosing the Right Authentication Method is not under your control
Although OAuth tokens are safer to use when compared to API keys, you can't use them unless the service-provider platform supports them.
Some platforms use API Keys as the authentication method, while some use OAuth Tokens.
For example, Hunter.io and ChatGPT uses API keys while Gmail and Google Sheets uses OAuth Tokens for authentication.
Some platforms like Google allows us to use both kinds of authentication depending on our convenience.
Spoiler Alert: The first automation we will be building during this course involve Google Sheets and Gmail for sending quotes. Both are Google products and both use OAuth authentication.
APIs are how platform-dependent automations are possible.
This also means that if a platform doesn't provide an API, we cannot build an automation around that platform's data.
For example, If Google Sheets doesn't have an API, we cannot access and use the platform's spreadsheet as part of our automation.
Instead, we have to go with its alternative like Airtable because it has an API.
Anyway, now that you understand API and its authentication methods, we will understand how tools like Make.com to help us create automations using APIs of different platforms.